Smishing is a form of phishing that uses fraudulent mobile text messages, a threat growing at an alarming rate. These social engineering attacks aim to trick victims into clicking malicious links, downloading malware, or sending money to cybercriminals. Smishing surged by 328% in 2020, and 76% of businesses were targeted in a single year. Let’s explore how to spot these threats, respond effectively, and prevent them in the future.
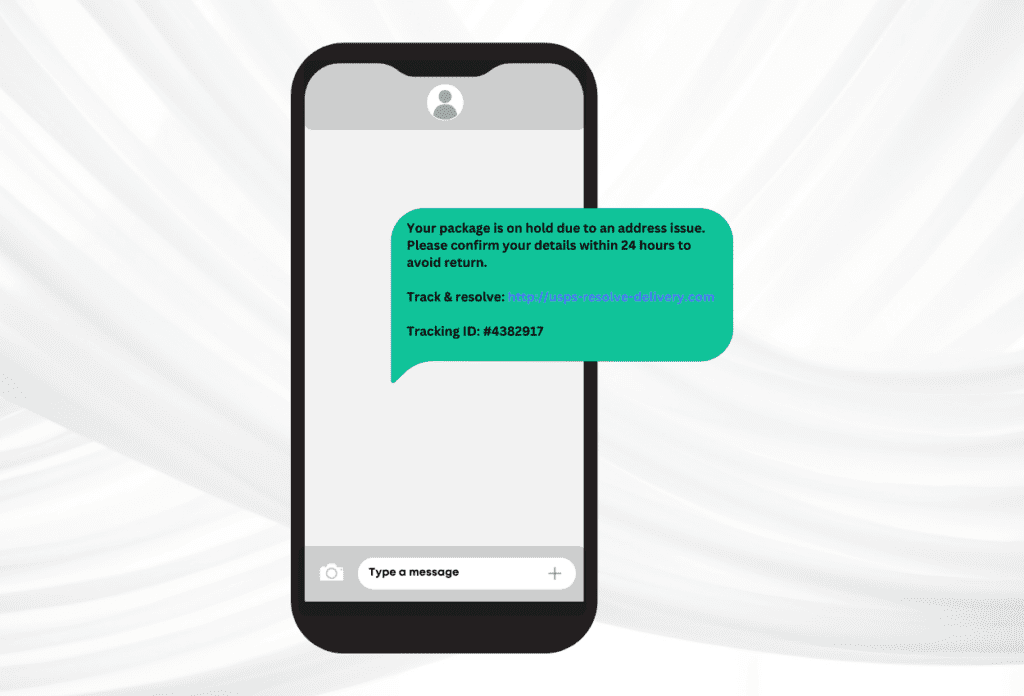
How To Spot Smishing Attacks
Identifying a smishing attack early is a crucial step in protecting yourself and your organization. These red flags will help you spot a potential threat:
Urgent/Fear-Based Messaging: Messages designed to incite panic, such as “Your account is locked!” or “Immediate action required!” are classic smishing tactics that pressure victims into acting without thinking. They often include suspicious links that can install malware on your device.
Requests For Personal Information: Messages from legitimate organizations will rarely, if ever, ask for any person’s information via text. Treat such requests with skepticism.
Too-Good-to-Be-True Offers: Promises of free prizes, discounts, or money are classic traps attackers will use to lure victims. If they ask for banking information or an up-front payment, that is a good way to spot a smishing attack.

Photo by Akrose Labs
How To Deal with Smishing Attacks
If you receive a suspicious text on your mobile device, follow these steps to minimize potential damage:
Do Not Respond: Avoid replying, clicking links, or providing any information. Replying lets the scammer know your number is active and you’re now a potential target. If you accidentally responded, ending the conversation, not replying in the future, and blocking and reporting the number is the best course of action.
Verify the Sender: If you get a text from someone or a business you aren’t expecting, proceed with caution. Always verify the sender, if the number is a contact of yours, or if you have a history with that number, is a good sign of it being real. For example, if it’s a package delivery text, check your records or contact the delivery service directly if you suspect anything.
Block and Report the Number: If you are at all uncertain of the authenticity of a text, blocking and reporting the number is a safe bet. Reporting the number will help prevent further messages from the sender and may assist others in avoiding similar scams.
Monitor Your Accounts: If you suspect you interacted with a smishing attempt, monitor the accounts for suspicious activity. Partnering with a managed cybersecurity and IT company can provide monitoring and safety precautions for these types of situations, ensuring a swift resolution to securing your accounts.

Photo by Rowan University
Ways To Prevent Future Smishing Attacks
Prevention is the best defense against cyberattacks. Strategies to help users stay protected from smishing are:
Enable MFA: Enabling Multi-Factor Authentication (MFA) will strengthen your accounts by requiring multiple forms of verification. Making it increasingly more difficult for an attacker to gain access to accounts even if they may have compromised your credentials.
Educate Yourself and Employees: Awareness is key. Learning and sharing information about smishing tactics will help train yourself and your team on how to recognize and deal with these threats.
Limit Personal Information Online: The more information a cybercriminal knows about you, the more tailored and customizable the message will be. Limiting personal information online only to the bare necessities is crucial in this increasing age of cyber-criminal activity.
Work with Cybersecurity Experts: A single person may stop a smishing scam. But for businesses with tens of hundreds of employees, all it takes is one to compromise a system. Kirkham IronTech offers solutions for any type of business; we ensure your any potential threats are swiftly disposed of. Our number one priority is safety.
Protect Yourself and Your Business from Smishing with Kirkham IronTech
Smishing attacks aren’t going to slow down anytime soon, and with basically everyone having a phone there is almost an infinite pool of victims for these cybercriminals. But you don’t have to face them alone. Kirkham IronTech offers comprehensive solutions that safeguard businesses and individuals from any cybersecurity and IT threat, including smishing. Our services range from 24/7 monitoring, employee training, threat detection and removal, spam filtering and monitoring, incident response planning, and more.
Whatever cybersecurity needs you may have; Kirkham IronTech has your back. We offer a free cybersecurity and infrastructure assessment to help you decide if our services are right for you!
Take Action Today!
Call Us: (479) 434-1400 – Speak with our cybersecurity specialists.
Visit Our Website: www.kirkhamirontech.com – Learn about our specialized services.
Email Us: info@kirkhamirontech.com – Let us help secure your business from smishing attacks.

 Tom Kirkham brings more than three decades of software design, network administration, and cybersecurity knowledge to organizations around the country. During his career, Tom has received multiple software design awards and founded other acclaimed technology businesses.
Tom Kirkham brings more than three decades of software design, network administration, and cybersecurity knowledge to organizations around the country. During his career, Tom has received multiple software design awards and founded other acclaimed technology businesses.