HOW WE DO IT
Kirkham IronTech Offers Solutions to Your IT & Cybersecurity Problems
Losing the trust of your clients could devastate your brand and your business almost immediately. With numerous vendors and an abundance of different security solutions, We’re able to provide more comprehensive cybersecurity and IT services than anyone on the market. This will keep your business and your clients’ data safe from cyber criminals.
Solutions Through Control
Empower Employees & Secure Your Data
We secure your data, servers, and more & teach employees how to stay secure.
- Business Continuity
- Continuous Cybersecurity Awareness Training
- Switch Management
- Firewall Management
- Router Management
- DNS Management
- Exchange Server Management
- Network Monitoring
- Email Management
Secure Your Physical Components
We create a plan to secure your physical assets in the workplace.
- Bio-metric authentication
- Server room control
- Server locks
- USB locks
24/7 Monitoring & Protection
We institute proactive measures and constant monitoring.
- EDR/XDR/Network Security
- Intrusion, detection and prevention
- Password Management
- Data Backup and disaster recovery
- SIEM
- ICS Monitoring and Management
- MFA/2FA
- VPN
- SASE
- Mobile Device Monitoring and Management
Security & Risk Assessment
Scheduling a security and infrastructure assessment will help you evaluate the effectiveness of your current security measures and identify potential vulnerabilities that could put your organization at risk.
This assessment will help you ensure the ongoing protection of your digital assets against cyber threats. Contact us today to schedule an appointment with one of our security experts.
Evaluate Your Current Security Posture
Our team of experts will assess your current security measures, policies, and procedures to determine how well they align with industry standards and best practices.
Identify Potential Risks
We will conduct a thorough analysis of your organization's network, systems, and applications to identify potential vulnerabilities that could be exploited by cybercriminals.
Develop a Comprehensive Risk Assessment Plan
Based on our findings, we will develop a customized risk management plan tailored to your organization's unique needs to help mitigate identified risks. We will implement the plan and mitigate the risks if you decide to move forward with us.
Gain Peace of Mind
By conducting regular security assessments, you can have peace of mind knowing that your organization is proactively addressing potential risks before they become real threats.
Systems Audit
A systems audit is a more in depth analysis of your IT network and helps you identify any potential vulnerabilities or areas for improvement in your current systems, allowing you to take steps to correct them before they become serious problems. It can also help you stay compliant with industry regulations and standards, reducing the risk of fines and other penalties.
This audit provides valuable insight into how your business is performing when it comes to information technology and cybersecurity measures, so that you can make informed decisions about future investments.
Alignment with Company Objectives
Uncover Cost Savings through Managed Services
Discover Security Gaps
In-Depth Discovery of Current Cybersecurity & IT State
Compliance & Regulatory Requirements
Continuous Review and Refinement
Industry Best Practices/Metrics
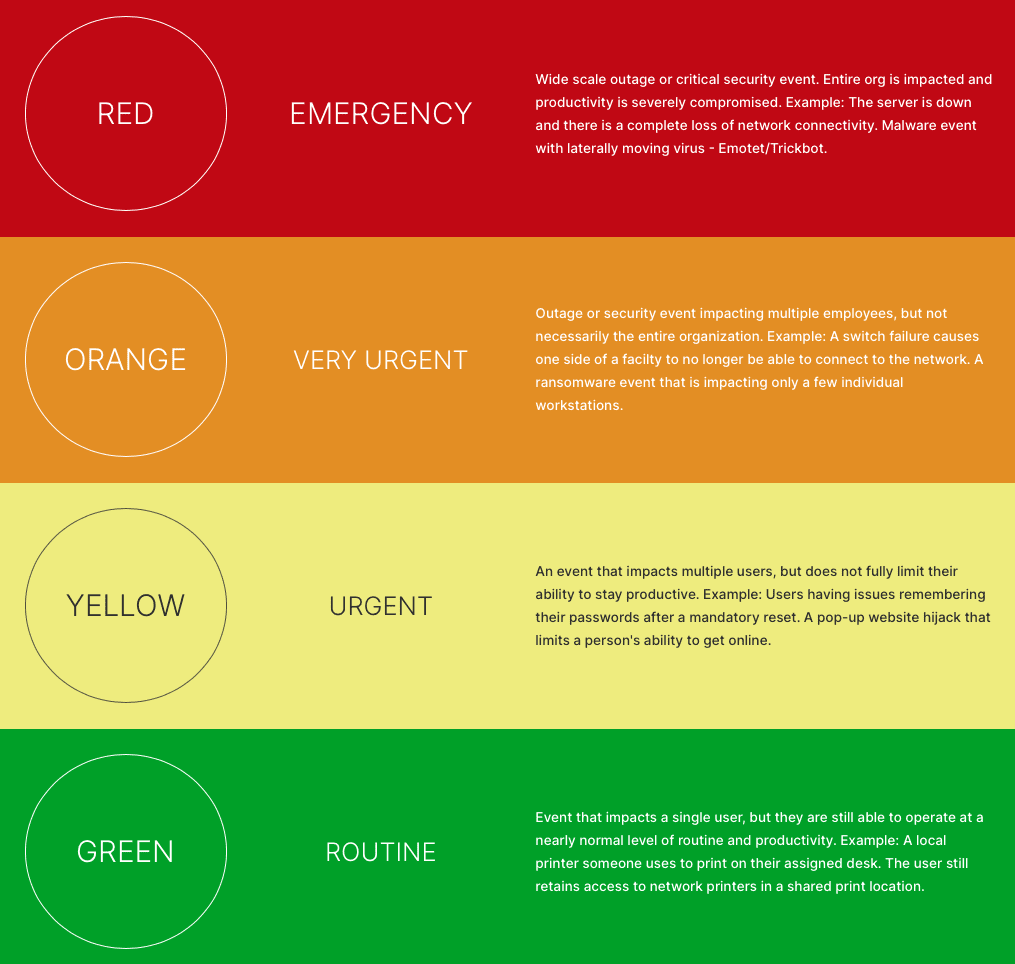
Support Triage
With our highly qualified and experienced team of IT professionals, we provide comprehensive, secure and reliable support that fits your needs.
We strive to ensure a fast resolution to any technical issues, so you can focus on other important things in your day-to-day operations.